Mac Privacy: Sandboxed Mac apps can record your screen at any time without you knowing
Update 2019-06-04 Apple has fixed this issue with macOS Catalina
Facts
Any Mac app, sandboxed or not sandboxed can:
- Take screenshots of your Mac silently without you knowing
- Access every pixel, even if the Mac app is in the background
- Use basic OCR software to read the text on the screen
- Access all connected monitors
What’s the worst that could happen?
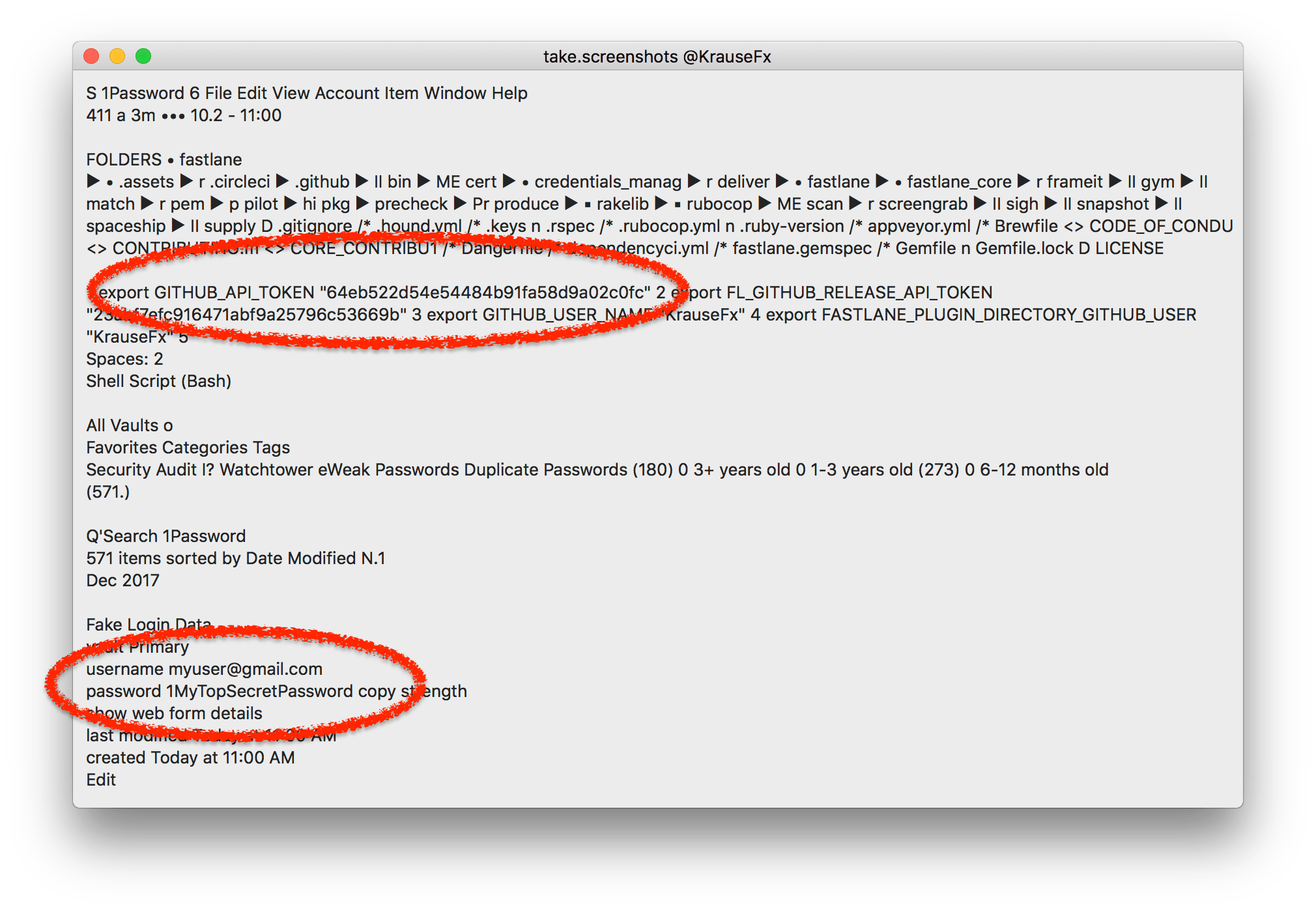
- Read password and keys from password managers
- Detect what web services you use (e.g. email provider)
- Read all emails and messages you open on your Mac
- When a developer is targeted, this allows the attacker to potentially access sensitive source code, API keys or similar data
- Learn personal information about the user, like their bank details, salary, address, etc.
Disclaimer
This project is a proof of concept and should not be used in production. The goal is to highlight a privacy loophole that can be abused by Mac apps.
How can I protect myself as a user?
To my knowledge there is no way to protect yourself as of now.
Proposal
There are lots of valid use-cases for Mac apps to record the screen, e.g. 1Password 2fA support, screen recording software or even simple screen sharing via your web browser or Skype. However there must be some kind of control:
- The App Store review process could verify the Sandbox entitlements for accessing the screen
- Put the user in charge with a permission dialog
- Additionally the user should be notified whenever an app accesses the screen.
Of course, I also filed a radar (rdar://37423927) to notify Apple about this issue.
How does it work?
A developer just needs to use CGWindowListCreateImage to generate a capture of the complete screen within an instant:
CGImageRef screenshot = CGWindowListCreateImage(
CGRectInfinite,
kCGWindowListOptionOnScreenOnly,
kCGNullWindowID,
kCGWindowImageDefault);
NSBitmapImageRep *bitmapRep = [[NSBitmapImageRep alloc] initWithCGImage:screenshot];
In my experiments, I piped the generated image over to a OCR library and was able to get all text that was rendered on the user’s machine.
Update 2019-06-04 Looks like Apple has fixed this issue with macOS Catalina
Similar projects I’ve worked on
I published more posts on how to access the camera, the user’s location data, their Mac screen and their iCloud password, check out krausefx.com/privacy for more.
Tags: mac, screenshot, privacy | Edit on GitHub
Introducing Overkill - Don't let iTunes interrupt your workflow
Update 2019-06-04 Looks like Apple has fixed this issue by deprecating iTunes
Exactly one year after the initial launch of Overkill as a shell script, after being #1 on ProductHunt, I’m extremely excited to announce that Overkill is now a native Mac app.
Did iTunes ever launch without you opening it? Use Overkill to instantly kill the iTunes process once it opened itself, so your workflow isn’t interrupted.
But Felix, you can use the check box to not launch iTunes when you connect your phone!
Yes, that is correct, but connecting a device to your Mac is only one of the many reasons when iTunes can’t wait to spread joy:
- You click the play/pause key while listening to a web-based music player (e.g. SoundCloud, YouTube)
- Someone sent you a link to an iOS app
- You click on a link on the web, and didn’t expect it to be a Music link
- You updated iTunes
- You launch iTunes by clicking on the icon by mistake
- You open a video/music file in Finder, and forgot to change the default app to VLC
- You connect Bluetooth headphones
Before Overkill
As you can see in the video above, iTunes would launch while you’re typing something, stealing the window focus, and making this sound we all love to hear.
With Overkill
With Overkill, you connect your iPhone to charge it, and you can still use your Mac.
Introducing Overkill for Mac
Overkill is a simple, elegant Mac app, that runs in the background and makes sure iTunes never interrupts your work.
And for those movie nights where you actually want to use iTunes, just click on Pause Overkill and enjoy the evening.
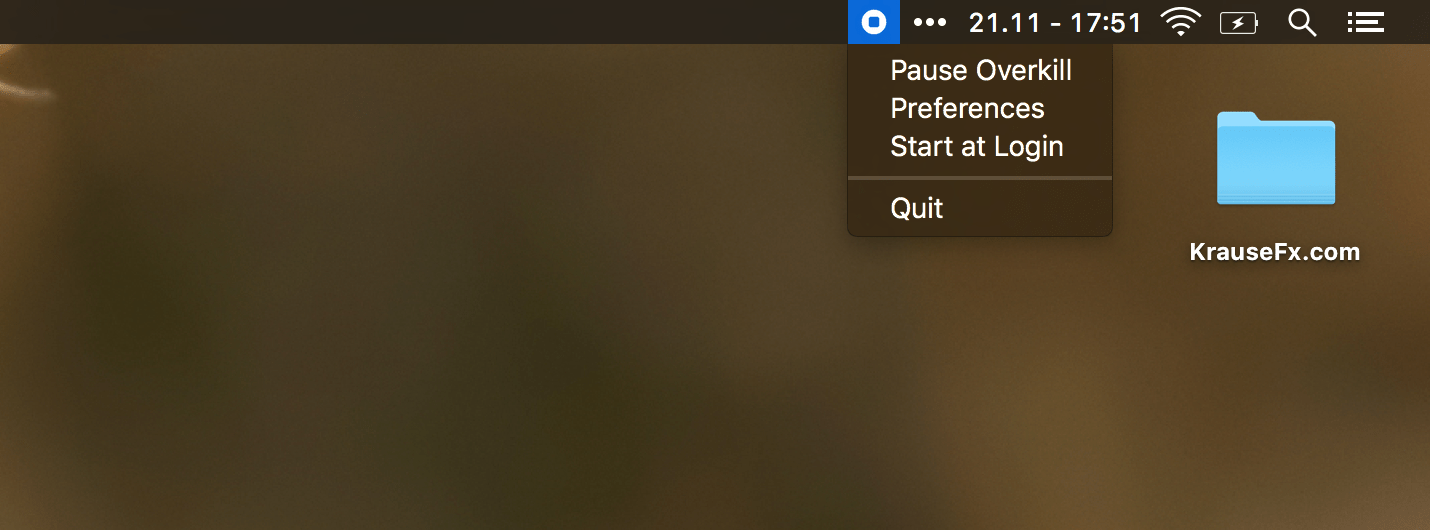
If you have other apps you don’t want to launch automatically (e.g. Photos app), you can add those apps to the Overkill list as well.
No installation required, just download Overkill from the link below, double click the Overkill icon, and you’re good to go!
Download Overkill Mac App
Unfortunately I couldn’t submit Overkill to the Mac App Store, as the sandboxing doesn’t allow the termination of other processes.
Features
- Runs silently in the background, and kills iTunes
- Easily pause Overkill if you want to use iTunes
- Support for both Dark and Light mode of the menu bar
- Supports auto start
- Supports any Mac app, e.g. add the Photos app to be killed also
- No CPU usage, no polling, no analytics, just 300 lines of native Mac code
Additionally, as most of the project I work on, Overkill is 100% open source under the MIT license:
Open on GitHub
Update 2019-06-04 Looks like Apple has fixed this issue by deprecating iTunes
Tags: itunes, overkill | Edit on GitHub
Introducing Major Key - Easily jot down quick notes
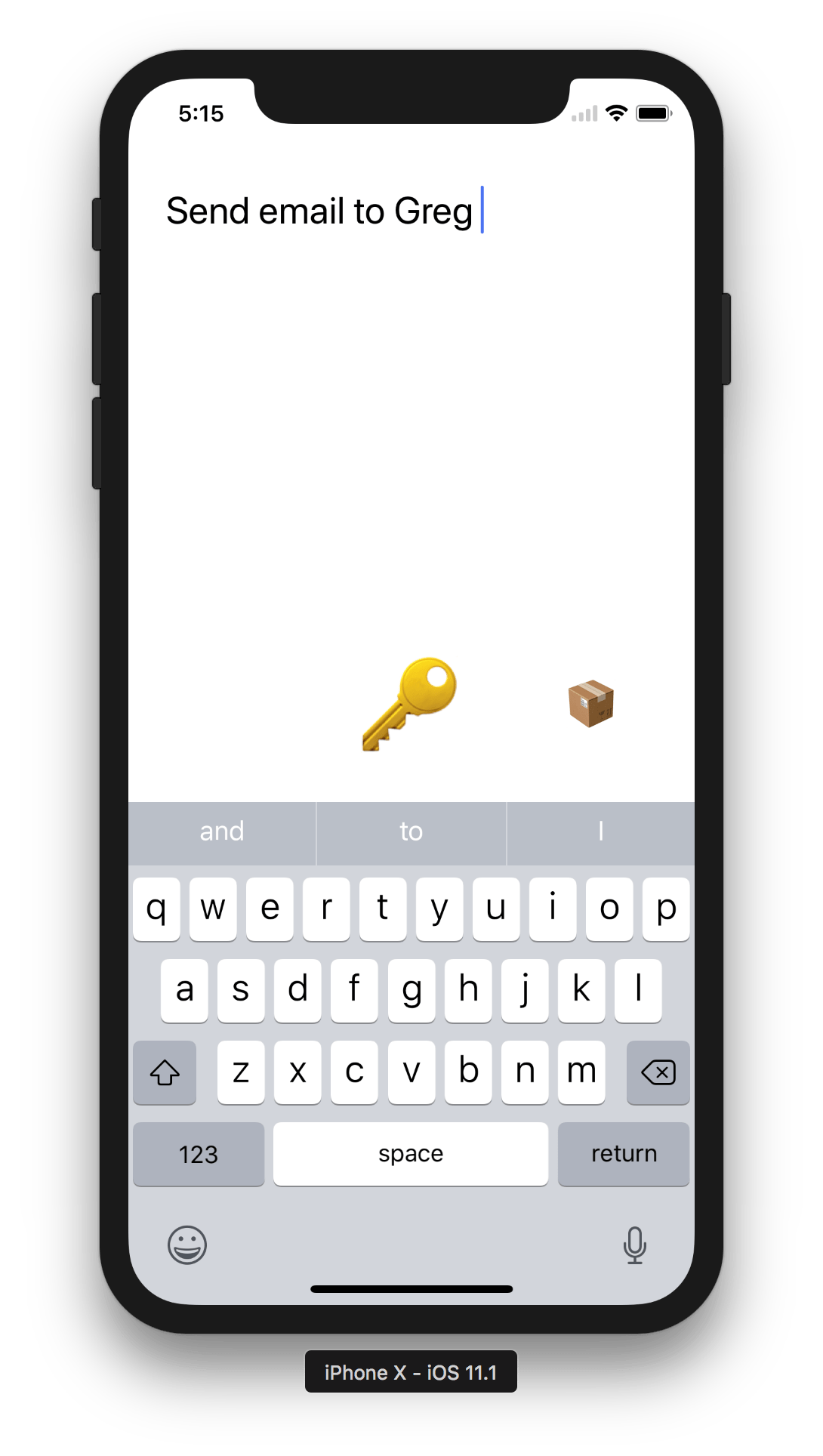
How often are you on the run, or hanging out with friends, only to suddenly think of this really important thing you need to do when you’re back home or back at work?
You want to jot down that thought as quickly as possible so you don’t forget, and you want to be reminded whenever you’re back on your computer.
Introducing Major Key, the best key
With far less than 100 lines of Swift code, this simple app does all you need:
- Unlock phone
- Launch Major Key 🔑
- Type the note
- Confirm
Within a second you’ll have the note in your email inbox. Extremely useful if you follow the inbox zero approach. All with no waiting times or animations.
Launch the app, write down a note, hit the 🔑 button and immediately have the note in your inbox.
Why a new app?
- Using any kind of Notes app works rather nicely, however involves overhead, and chances are you forget on checking the notes app when you’re back on your Mac.
- Sending yourself an email with any email client involves extra work, as you need to start typing your email, and you get to see your inbox (similar idea)
- The IFTTT Notes app was perfect, however it was discontinued, and the new IFTTT app causes problems on the iPhone X due to abusing Web Clips to make it work.
🔑 Major Key is not available in the App Store, but is open source, and super easy to install if you’re a developer. If interest is there, I could also publish the app to the store.
Open on GitHub
Tags: notes, ifttt | Edit on GitHub
iOS Privacy: watch.user - Access both iPhone cameras any time your app is running
Update 2020-06-22 Apple has fixed this issue with iOS 14
Facts
Once you grant an app access to your camera, it can
- access both the front and the back camera
- record you at any time the app is in the foreground
- take pictures and videos without telling you
- upload the pictures/videos it takes immediately
- run real-time face recognition to detect facial features or expressions
Have you ever used a social media app while using the bathroom? 🚽
All without indicating that your phone is recording you and your surrounding, no LEDs, no light or any other kind of indication.
Disclaimer
This project is a proof of concept and should not be used in production. The goal is to highlight a privacy loophole that can be abused by iOS apps.
What can an iOS app do?
iOS users often grant camera access to an app soon after they download it (e.g. to add an avatar or send a photo). These apps, like a messaging app or any news-feed-based app, can easily track the users face, take pictures, or live stream the front and back camera, without the user’s consent.
- Get full access to the front and back camera of an iPhone/iPad any time your app is running in the foreground
- Use the front and the back camera to know what your user is doing right now and where the user is located based on image data
- Upload random frames of the video stream to your web service, and run a proper face recognition software, which enables you to
- Find existing photos of the person on the internet
- Learn how the user looks like and create a 3d model of the user’s face
- Live stream their camera onto the internet (e.g. while they sit on the toilet), with the recent innovation around faster internet connections, faster processors and more efficient video codecs it’s hard to detect for the average user
- Estimate the mood of the user based on what you show in your app (e.g. news feed of your app)
- Detect if the user is on their phone alone, or watching together with a second person
- Recording stunning video material from bathrooms around the world, using both the front and the back camera, while the user scrolls through a social feed or plays a game
- Using the new built-in iOS 11 Vision framework, every developer can very easily parse facial features in real-time like the eyes, mouth, and the face frame
How can I protect myself as a user?
There are only a few things you can do:
- The only real safe way to protect yourself is using camera covers: There is many different covers available, find one that looks nice for you, or use a sticky note (for example).
- You can revoke camera access for all apps, always use the built-in camera app, and use the image picker of each app to select the photo (which will cause you to run into a problem I described with detect.location).
- To avoid this as well, the best way is to use Copy & Paste to paste the screenshot into your messaging application. If an app has no copy & paste support, you’ll have to either expose your image library, or your camera.
It’s interesting that many people cover their camera, including Mark Zuckerberg.
Proposal
How can the root of the problem be fixed, so we don’t have to use camera covers?
- Offer a way to grant temporary access to the camera (e.g. to take and share one picture with a friend on a messaging app), related to detect.location.
- Show an icon in the status bar that the camera is active, and force the status bar to be visible whenever an app accesses the camera
- Add an LED to the iPhone’s camera (both sides) that can’t be worked around by sandboxed apps, which is the elegant solution that the MacBook uses
I reported the issue to Apple with rdar://35116272.
About the demo
I didn’t submit the demo to the App Store; however, you can very easily clone the repo and run it on your own device.
- You first have to take a picture that gets “posted” on the fake “social network” in the app
- At this point, you’ve granted full access to both of your cameras every time the app is running
- You browse through a news feed
- After a bit of scrolling, you’ll suddenly see pictures of yourself, taken a few seconds ago while you scrolled through the feed
- You realize you’ve been recorded the whole time, and with it, the app ran a face recognition algorithm to detect facial features.
You might say
Oh, obviously, I never grant camera permissions!

However, if you’re using a messaging service, like Messenger, WhatsApp, Telegram or anything else, chances are high you already granted permission to access both your image library (see detect.location) and your camera. You can check which apps have access to your cameras and photo library by going to Settings > Privacy.
The full source code is available on GitHub.
How does the demo app get access to the camera?
Once you take and post one picture or video via a social network app, you grant full access to the camera, and any time the app is running, the app can use the camera.
What’s the screenshot on the right
As part of iOS 11, there is now an easy to use Vision framework, that allows developers to easily track faces. The screenshot shows that it’s possible to get some basic emotions right, so I wrote a very basic mapping of a user’s face to the corresponding emoji as a proof of concept. You can see the highlighted facial features, and the detected emoji at the bottom.
Similar projects I’ve worked on
I published more posts on how to access the camera, the user’s location data, their Mac screen and their iCloud password, check out krausefx.com/privacy for more.
Special thanks to Soroush, who came up with the initial idea for this write-up.
Open on GitHub
Tags: ios, privacy, phishing, camera, video | Edit on GitHub